Mitigate CVE-2022-27925 on Nginx: Difference between revisions
(Created page with "{{BC|Certified}} __FORCETOC__ <div class="col-md-12 ibox-content"> = Mitigate CVE-2022-27925 on Nginx = <hr> {{KB|{{WIP}}|{{ZCS 9.0}}|{{ZCS 8.8}}}} <hr> ====Problem==== ZCS...") |
(No difference)
|
Revision as of 20:08, 22 August 2022
Mitigate CVE-2022-27925 on Nginx
Problem
ZCS versions before 8.8.15 Patch 31 and 9.0.0 Patch 24 are vulnerable to "CVE-2022-27925".
Accessing the below webmail URL of a vulnerable system returns a "500 Server Error".
curl https://mail.example.com/service/extension/backup/mboximport
<html>
<head>
<meta http-equiv="Content-Type" content="text/html;charset=utf-8"/>
<title>Error 500 Server Error</title>
</head>
<body><h2>HTTP ERROR 500</h2>
<p>Problem accessing /service/extension/backup/mboximport. Reason:
<pre>Server Error</pre></p>
</body>
</html>
Solution
On the old ZCS versions, we have to modify Nginx templates on proxy servers to mitigate "CVE-2022-27925".
1) Take a backup of current templates directory "/opt/zimbra/conf/nginx/templates".
sudo cp -pvr /opt/zimbra/conf/nginx/templates /opt/zimbra/conf/nginx/templates.`date +%Y%m%d%H%M%S`.bak
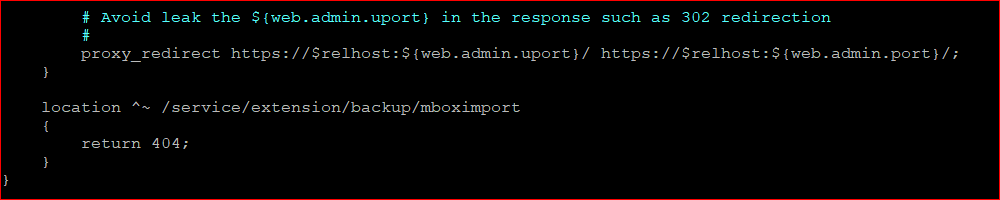
2) Modify both admin templates and the following location block at the end before closing the server block.
-------------------
location ^~ /service/extension/backup/mboximport
{
return 404;
}
-------------------
Admin template files:
/opt/zimbra/conf/nginx/templates/nginx.conf.web.admin.default.template /opt/zimbra/conf/nginx/templates/nginx.conf.web.admin.template
For a better understanding take a look at the following screenshots of the new location block.
3) Now modify the following HTTP and HTTPS templates, and add the same new location block at the end before the last "include" line.
HTTP and HTTPS template files:
/opt/zimbra/conf/nginx/templates/nginx.conf.web.http.default.template /opt/zimbra/conf/nginx/templates/nginx.conf.web.http.template /opt/zimbra/conf/nginx/templates/nginx.conf.web.https.default.template /opt/zimbra/conf/nginx/templates/nginx.conf.web.https.template
4) Restart Proxy and Memcache services.
su - zimbra zmproxyctl restart zmmemcachedctl restart
5) After applying these changes, requests for mboximport returns a 404 Error.
curl https://mail.example.com/service/extension/backup/mboximport
<html>
<head> <title>404 Not Found</title> </head>
<body>
<center><h1>404 Not Found</h1></center>
<hr><center>nginx</center>
</body>
</html>
| Submitted by: Heera Singh Koranga |